اخبار مرتبط به PC (سخت افزار و نرم افزار) اینجا قرار گرفته میشه . مباحث متفرقه از جمله vs ، سیاسی و .... ممنوع ـه در صورت تخطی برخورد میشه.
با تشکر
با تشکر


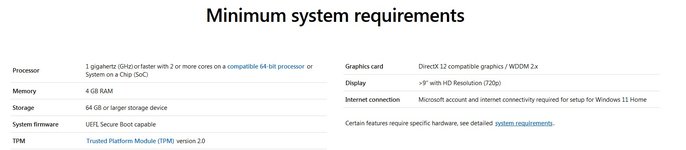
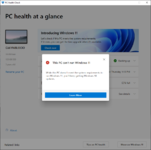
To check if your current Windows 10 PC is eligible for the free upgrade to Windows 11, visit Windows.com to download the PC Health Check app
DirectStorage requires 1 TB or greater NVMe SSD to store and run games that uses the "Standard NVM Express Controller" driver and a DirectX 12 Ultimate GPU
DirectX 12 Ultimate is available with supported games and graphics chips
Apparently the latest news suggest Windows 11 will be launched / goes live when Intel Alder Lake is launched in November, suggesting a 11th of November release
این داستان tpm چیه پیاده کردن؟
Trusted Platform Module (TPM) technology is designed to provide hardware-based, security-related functions. A TPM chip is a secure crypto-processor that is designed to carry out cryptographic operations. The chip includes multiple physical security mechanisms to make it tamper resistant, and malicious software is unable to tamper with the security functions of the TPM. Some of the key advantages of using TPM technology are that you can
TPM-based keys can be configured in a variety of ways. One option is to make a TPM-based key unavailable outside the TPM. This is good to mitigate phishing attacks because it prevents the key from being copied and used without the TPM. TPM-based keys can also be configured to require an authorization value to use them. If too many incorrect authorization guesses occur, the TPM will activate its dictionary attack logic and prevent further authorization value guesses