آخرین ویرایش:
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
گزینههای بیشتر
مشارکت کنندگان در این گفتگوFifa 15 for PS4 is Dumped and Decrypted with Precompiled Payload
Previously we reported on Decrypted PS4 Games and PKG Files, PS4 Package Updates and PS4 Tunables and now PlayStation 4 developer @zecoxao (Twitter) tweeted that Fifa 15 has been dumped and decrypted with a precompiled payload for developers available below! :thumbsupxf2:
Download: DumpFile (CUSA00722) (319.69 KB) / DumpFile (CUSA00564) (319.69 KB) / DumpFile (CUSA01110) (319.69 KB) / Fifa15_DumpFile_Payload.rar (149 KB - Mirror by Fosi of e✘treme-Modding)
According to notzecoxao, the files will the files will be output to /mnt/usb0 (rightmost port), and below are the related Tweets:

..
Previously we reported on Decrypted PS4 Games and PKG Files, PS4 Package Updates and PS4 Tunables and now PlayStation 4 developer @zecoxao (Twitter) tweeted that Fifa 15 has been dumped and decrypted with a precompiled payload for developers available below! :thumbsupxf2:
Download: DumpFile (CUSA00722) (319.69 KB) / DumpFile (CUSA00564) (319.69 KB) / DumpFile (CUSA01110) (319.69 KB) / Fifa15_DumpFile_Payload.rar (149 KB - Mirror by Fosi of e✘treme-Modding)
According to notzecoxao, the files will the files will be output to /mnt/usb0 (rightmost port), and below are the related Tweets:
..
اینم خبر مهمی که همه منتظرش بودید ریلیز شدن وب کیت برای ps4 برای فریمور 4.0x به پایین.(البته این اول راهه هنوز مونده تا هک کامل و صرفا یه راه نفوذ هست)
برای تست هم باید با مرورگر کنسول به ادرس JailbreakMe PS4 4.0x برین.
Hacker qwertyoruiop just released a Webkit exploit for PS4s running on Firmware 4.0x.
According to the hacker, the exploit works up to firmware 4.06 at least (update: users have independently confirmed this also works on firmware 4.07), but it has been patched in firmware 4.50. People have confirmed the exploit seems to behave as expected on their 4.0x PS4, others have confirmed it works on firmware 3.55 as well.
Users who want to test the vulnerability can point their PS4 browser to http://rce.party/ps4/.
This is what this should look like if your PS4 is vulnerable to the exploit:
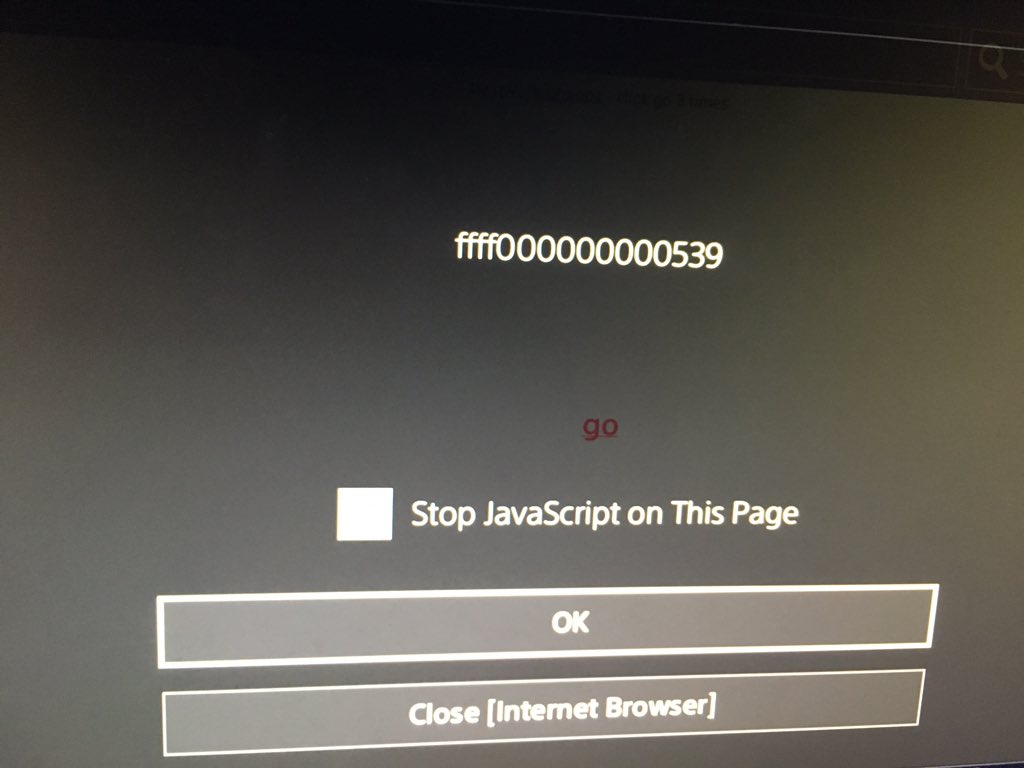
screenshot by @DJShinter
On firmware 4.50, this is the (self explanatory) error you’ll get:
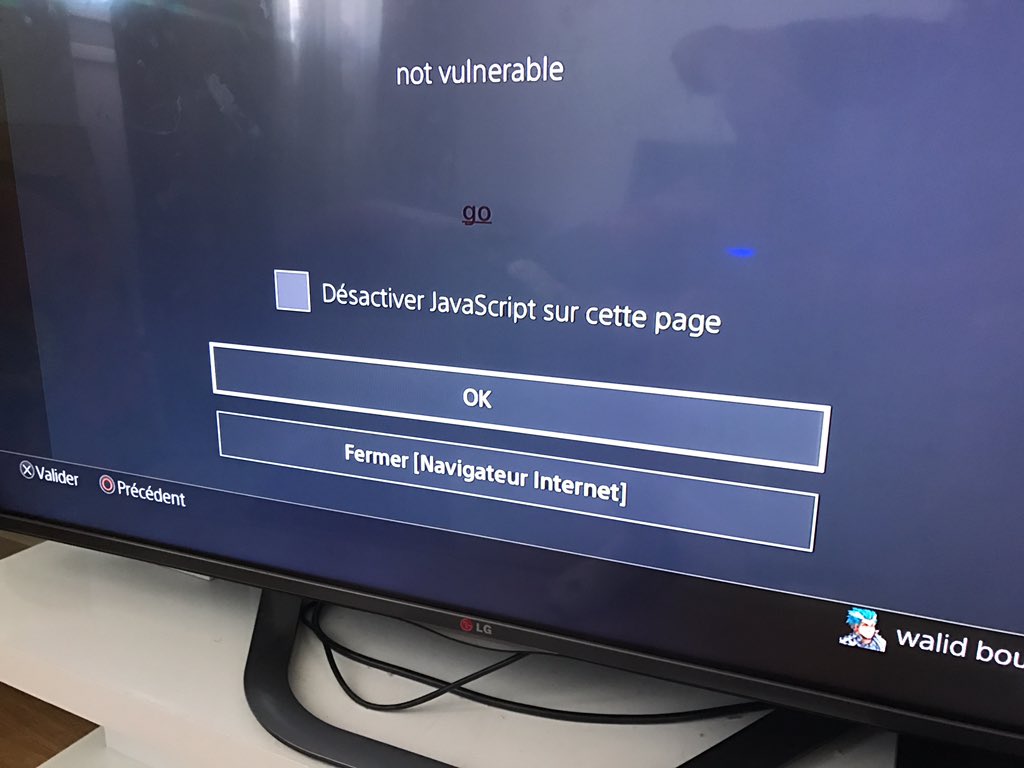
Screenshot by @walidboy23
Details on the PS4 4.0x Webkit exploit
I assume people can start digging into the details of the exploit, however qwertyoruiop gave the precision that the exploit is triggered by a Use After Free vulnerability. We might see a writeup on the vulnerability at some point.
منبع
PS4 4.0x Webkit exploit released - Wololo.net
برای تست هم باید با مرورگر کنسول به ادرس JailbreakMe PS4 4.0x برین.
Hacker qwertyoruiop just released a Webkit exploit for PS4s running on Firmware 4.0x.
According to the hacker, the exploit works up to firmware 4.06 at least (update: users have independently confirmed this also works on firmware 4.07), but it has been patched in firmware 4.50. People have confirmed the exploit seems to behave as expected on their 4.0x PS4, others have confirmed it works on firmware 3.55 as well.
Users who want to test the vulnerability can point their PS4 browser to http://rce.party/ps4/.
This is what this should look like if your PS4 is vulnerable to the exploit:

screenshot by @DJShinter
On firmware 4.50, this is the (self explanatory) error you’ll get:

Screenshot by @walidboy23
Details on the PS4 4.0x Webkit exploit
I assume people can start digging into the details of the exploit, however qwertyoruiop gave the precision that the exploit is triggered by a Use After Free vulnerability. We might see a writeup on the vulnerability at some point.
منبع
PS4 4.0x Webkit exploit released - Wololo.net
برای فریمور های 3.55 تا 4.07 اومده.باید منتظر کرنل باشیم تا به صورت عمومی منتشر بشه و کار هک یه سره شه.اینم یه امیدواری برای اون دسته از افراد که فریمور بالاتر از 4 دارن.اونایی که فریمور 4.50 کردن سونی این باگو فیکس کرده
Saeedrz70
کاربر سایت
باید صبر کرد تا کنسول روی ورژن های خاصی جیلبریک بشهحالا چطور دانگرید کنیم
بعد ممکنه ابزارهایی واسه دانگرید ( سخت افزاری/نرم افزاری) ارائه بشه
هنوز که اتفاق خاصی نیفتاده
PS4 NIDs and PS3 NIDs Added to Hashcat Bruteforcer by Jarveson
Following the PS3 FNIDS Python Scripts by PlayStation developer @zecoxao, today he let us know on Twitter that jarveson added PS4 NIDs and PS3 NIDs to his Hashcat bruteforcer password recovery utility. :winkxf2:
Download: Hashcat v3.40 / PS4 NIDs / PS3 NIDs
Intended for developers, the NIDs can be used with the attack tool to determine PlayStation 4 and PlayStation 3 System Firmware function names.
From the README.md: hashcat
hashcat is the world's fastest and most advanced password recovery utility, supporting five unique modes of attack for over 200 highly-optimized hashing algorithms.
hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, Windows, and OSX, and has facilities to help enable distributed password cracking.
PS4 NIDs
include/interface.h

Following the PS3 FNIDS Python Scripts by PlayStation developer @zecoxao, today he let us know on Twitter that jarveson added PS4 NIDs and PS3 NIDs to his Hashcat bruteforcer password recovery utility. :winkxf2:
Download: Hashcat v3.40 / PS4 NIDs / PS3 NIDs
Intended for developers, the NIDs can be used with the attack tool to determine PlayStation 4 and PlayStation 3 System Firmware function names.
From the README.md: hashcat
hashcat is the world's fastest and most advanced password recovery utility, supporting five unique modes of attack for over 200 highly-optimized hashing algorithms.
hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, Windows, and OSX, and has facilities to help enable distributed password cracking.
PS4 NIDs
include/interface.h
mafia1234
کاربر سایت
خب چیه اینPS4 NIDs and PS3 NIDs Added to Hashcat Bruteforcer by Jarveson
Following the PS3 FNIDS Python Scripts by PlayStation developer @zecoxao, today he let us know on Twitter that jarveson added PS4 NIDs and PS3 NIDs to his Hashcat bruteforcer password recovery utility. :winkxf2:
Download: Hashcat v3.40 / PS4 NIDs / PS3 NIDs
Intended for developers, the NIDs can be used with the attack tool to determine PlayStation 4 and PlayStation 3 System Firmware function names.
From the README.md: hashcat
hashcat is the world's fastest and most advanced password recovery utility, supporting five unique modes of attack for over 200 highly-optimized hashing algorithms.
hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, Windows, and OSX, and has facilities to help enable distributed password cracking.
PS4 NIDs
include/interface.h

Mahdi444
کاربر سایت
دوستان پیشنهاد میدم ترجمهی خبرها رو بزارین نه اینکه اول اصل خبر گذاشته بشه بعد یه نفر بیاد بگه که ترجمه کنید بعدش یه ترجمهی خلاصهی گذاشته بشه :«|
Sent from my HTC M8Sw using Tapatalk
Sent from my HTC M8Sw using Tapatalk
سلام
من انگلیسی بلد نیستم . دوستانی که بلد هستن .کمکی بکنند تا بدونیم کی به کیه و کی هک میشه این ps4
دورغ ۱۳ بدر و دروغ اوریل
معلوم نیست .. ایا راهی پیدا شده برای هک یا نه ..مسله اینه
Will the 4.50 PS4 Jailbreak be released?
PS4 Jailbreak: qwertyoruiop progresses on PS4 Webkit hack, states he has a 4.50 kernel exploit - Wololo.net

من انگلیسی بلد نیستم . دوستانی که بلد هستن .کمکی بکنند تا بدونیم کی به کیه و کی هک میشه این ps4
دورغ ۱۳ بدر و دروغ اوریل
معلوم نیست .. ایا راهی پیدا شده برای هک یا نه ..مسله اینه
Will the 4.50 PS4 Jailbreak be released?
PS4 Jailbreak: qwertyoruiop progresses on PS4 Webkit hack, states he has a 4.50 kernel exploit - Wololo.net

m.a.t
Loyal Member
این یه exploit مربوط به مرورگر کنسول ـه که روی نسخه 1.76 هم مشابه اش بود و اجازه میده یه سری کارها رو روی کرنل انجام داد.سلام
من انگلیسی بلد نیستم . دوستانی که بلد هستن .کمکی بکنند تا بدونیم کی به کیه و کی هک میشه این ps4
دورغ ۱۳ بدر و دروغ اوریل
معلوم نیست .. ایا راهی پیدا شده برای هک یا نه ..مسله اینه
Will the 4.50 PS4 Jailbreak be released?
PS4 Jailbreak: qwertyoruiop progresses on PS4 Webkit hack, states he has a 4.50 kernel exploit - Wololo.net

روی 1.76 نتیجه این exploit این بود که لینوکس نصب کردن و کذا و کذا.
حالا اگر Jailbreak هم بشه، این رو نمی دونم. اما روی 1.76 که چیزی دست خلق الله رو نگرفت.
mehdizadeh
کاربر سایت
اینو هم ترحمه کنید ببینیم جی مگه؟
PS4 Webkit hack: SpecterDev explains 4.0x exploit, releases updated PoC with multi-FW support
BY WOLOLO · APRIL 8, 2017
A few days ago, hacker qwertyoruiop released a Webkit exploit for the PS4, compatible up to firmware 4.07 included. He has since then improved the exploit to include a ROP Chain and basic syscalls, but providing only compatibility for 4.06, the firmware on which he is personally working.
Developer SpecterDev, self described as a programmer interested in exploitation and infosec, and who in the past has provided accurate analysis of other PS4 hacks, has released a writeup of qwertyoruiop’s exploit, and released his own version of the exploit, with added compatibility for multiple firmwares.
SpecterDev’s Proof of concept builds on top of the initial exploit and adds Rop/gadget support for firmwares 3.50, 3.55, 3.70, 4.00, and 4.07 (in addition to 4.06 which was already supported in the initial PoC). Visibly no support for firmware 4.05, but a quick glance at the source tells me it shouldn’t be too difficult to add for people who feel like it.
Additionally, the developer released a writeup about qwertyoruiop,s exploit, and it’s a great read. What’s particularly interesting here is that SpecterDev, as he states himself, is still fairly new to exploits in general and webkit in particular (although you will see from the writeup that he is being humble here
 ). As a result, the write up is reasonably easy to read because the author makes no unrealistic assumptions on the technical level of the reader. I’d say it’s a great introduction to understanding how the exploit works, if you have basic coding/system knowledge.
). As a result, the write up is reasonably easy to read because the author makes no unrealistic assumptions on the technical level of the reader. I’d say it’s a great introduction to understanding how the exploit works, if you have basic coding/system knowledge.
You can read SpecterDev’s writeup here.

Source qwertyoruiop
Download/test the Webkit Exploit for 3.50, 3.55, 3.70, 4.00, 4.06, 4.07
You can download the source for the exploit on SpecterDev’s github here. Keep in mind that this is a rewrite of qwertyoruiop’s original exploit which will probably remain the source of truth and of major updates for now.
To run the exploit from the source (from SpecterDev’s readme):
setup a web-server on localhost using xampp or any other program and setup these files in a directory. You can then go to your computer’s local IPv4 address (found by running ipconfig in cmd.exe) and access the exploit.
منبع:
PS4 Webkit hack: SpecterDev explains 4.0x exploit, releases updated PoC with multi-FW support - Wololo.net
PS4 Webkit hack: SpecterDev explains 4.0x exploit, releases updated PoC with multi-FW support
BY WOLOLO · APRIL 8, 2017
A few days ago, hacker qwertyoruiop released a Webkit exploit for the PS4, compatible up to firmware 4.07 included. He has since then improved the exploit to include a ROP Chain and basic syscalls, but providing only compatibility for 4.06, the firmware on which he is personally working.
Developer SpecterDev, self described as a programmer interested in exploitation and infosec, and who in the past has provided accurate analysis of other PS4 hacks, has released a writeup of qwertyoruiop’s exploit, and released his own version of the exploit, with added compatibility for multiple firmwares.
SpecterDev’s Proof of concept builds on top of the initial exploit and adds Rop/gadget support for firmwares 3.50, 3.55, 3.70, 4.00, and 4.07 (in addition to 4.06 which was already supported in the initial PoC). Visibly no support for firmware 4.05, but a quick glance at the source tells me it shouldn’t be too difficult to add for people who feel like it.
Additionally, the developer released a writeup about qwertyoruiop,s exploit, and it’s a great read. What’s particularly interesting here is that SpecterDev, as he states himself, is still fairly new to exploits in general and webkit in particular (although you will see from the writeup that he is being humble here

You can read SpecterDev’s writeup here.

Source qwertyoruiop
Download/test the Webkit Exploit for 3.50, 3.55, 3.70, 4.00, 4.06, 4.07
You can download the source for the exploit on SpecterDev’s github here. Keep in mind that this is a rewrite of qwertyoruiop’s original exploit which will probably remain the source of truth and of major updates for now.
To run the exploit from the source (from SpecterDev’s readme):
setup a web-server on localhost using xampp or any other program and setup these files in a directory. You can then go to your computer’s local IPv4 address (found by running ipconfig in cmd.exe) and access the exploit.
منبع:
PS4 Webkit hack: SpecterDev explains 4.0x exploit, releases updated PoC with multi-FW support - Wololo.net
فقط منبع بذارید دوستانی که بلدن میان ترجمه میکنناینو هم ترحمه کنید ببینیم جی مگه؟
منبع:
PS4 Webkit hack: SpecterDev explains 4.0x exploit, releases updated PoC with multi-FW support - Wololo.net
m.a.t
Loyal Member
اون exploitـی بود که چند روز قبل خبرش اومد و فلان و بیسار...اینو هم ترحمه کنید ببینیم جی مگه؟
PS4 Webkit hack: SpecterDev explains 4.0x exploit, releases updated PoC with multi-FW support
BY WOLOLO · APRIL 8, 2017
A few days ago, hacker qwertyoruiop released a Webkit exploit for the PS4, compatible up to firmware 4.07 included. He has since then improved the exploit to include a ROP Chain and basic syscalls, but providing only compatibility for 4.06, the firmware on which he is personally working.
Developer SpecterDev, self described as a programmer interested in exploitation and infosec, and who in the past has provided accurate analysis of other PS4 hacks, has released a writeup of qwertyoruiop’s exploit, and released his own version of the exploit, with added compatibility for multiple firmwares.
SpecterDev’s Proof of concept builds on top of the initial exploit and adds Rop/gadget support for firmwares 3.50, 3.55, 3.70, 4.00, and 4.07 (in addition to 4.06 which was already supported in the initial PoC). Visibly no support for firmware 4.05, but a quick glance at the source tells me it shouldn’t be too difficult to add for people who feel like it.
Additionally, the developer released a writeup about qwertyoruiop,s exploit, and it’s a great read. What’s particularly interesting here is that SpecterDev, as he states himself, is still fairly new to exploits in general and webkit in particular (although you will see from the writeup that he is being humble here ). As a result, the write up is reasonably easy to read because the author makes no unrealistic assumptions on the technical level of the reader. I’d say it’s a great introduction to understanding how the exploit works, if you have basic coding/system knowledge.
You can read SpecterDev’s writeup here.

Source qwertyoruiop
Download/test the Webkit Exploit for 3.50, 3.55, 3.70, 4.00, 4.06, 4.07
You can download the source for the exploit on SpecterDev’s github here. Keep in mind that this is a rewrite of qwertyoruiop’s original exploit which will probably remain the source of truth and of major updates for now.
To run the exploit from the source (from SpecterDev’s readme):
setup a web-server on localhost using xampp or any other program and setup these files in a directory. You can then go to your computer’s local IPv4 address (found by running ipconfig in cmd.exe) and access the exploit.
منبع:
PS4 Webkit hack: SpecterDev explains 4.0x exploit, releases updated PoC with multi-FW support - Wololo.net
یه بنده خدایی اومده روش کار اون رو توضیح داده و خودش هم یه تغییراتی روش داده و منتشر کرده. و البته این اکسپلویت روی چند تا ورژن مختلف فیرم ور هم اجرا میشه.
کماکان اینا هیچ روزنه امیدی به سمت کپی خور شدن باز نمی کنه. فکر کنم داره 2 سال از کشف اکسپلویت مشابه روی نسخه 1.76 می گذره
و هیچ ثمره ملموسی دست ما رو نگرفته
یه خبری شده لطفا یکی ترجمه کنه
تیم دانگل کبرا :::: تیم ما از روش "هک برزیلی" دانلود بازی به روی PS4 با سیستم عامل 4.50 را پیدا کرده
Brazilian PS4 Method for 4.50 Firmware Rumor by Cobra ODE Reseller
Since correcting concerns here last month while others go unnoticed, we've included 'Rumor' in this article's title per our updated Site News Posting Guidelines to reflect that this topic should be considered a RUMOR as such.
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:stop:
Now that everyone is clear on that... recently we've heard PS4 4.50 injection rumors reminiscent of those on PS3, so I replied to a few private messages with essentially what you see posted in my reply HERE asking someone who knows more to come forward.
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:notworthyxf2:
Those who've been following the PS4 scene are already familiar with PlayStation 4 GameSharing and the Russian / Egyptian / Xmax Katsu hardware variants of it, but what we found out about today from @Bassabov in the PSXHAX Shoutbox is that official Team Cobra ODE Reseller MagicDevice.ru (see HERE as Cobra's fly-by-night domain is suspended at the time of writing) claims to have revived the Brazilian PS4 GameSharing Method for 4.50 Firmware... that's the current RUMOR anyway!
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:unsurexf2:
Here's what their page states, to quote roughly translated: "PS4: The Brazilian method is the return News - PS4 (10/04/2017 15:45)
Great news! Our team revived the "Brazilian method" of downloading games on the PS4 with the firmware 4.50.
And so, again the Brazilian method works!
1. Fast download of games to your PS4 (from 1 to 3 days)
2. Any firmware, including 4.50
3. Any model PS4 (Fat, Slim, PRO) and any region.
4. Download both to internal and external HDD
5. While ONLINE NO !!! (But we are working on this issue)
6. To download games by our method, the attachment is disassembled!
7. Guarantee from our SC!
A list of games in the PS4 section of our site. We are waiting for orders!"
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:stop: Needless to say, don't pay anyone for harddrives with preloaded PS4 games on them regardless of whether they are rumored to be working on PS4 4.50 Firmware or not... and also don't pay $5,000 (~5 BTC) for the method being used by dark web con-artists and opportunists.
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:slap:
If this RUMOR ends up being legitimate (hopefully Team Cobra ODE screens their business associates to some degree of credibility before including them on their official reseller list
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:cautiousxf2 all it will take is someone with the necessary files or information to reveal it in the PlayStation 4 scene for FREE, and thanks again to @Bassabov for sharing what you knew about it with us!
all it will take is someone with the necessary files or information to reveal it in the PlayStation 4 scene for FREE, and thanks again to @Bassabov for sharing what you knew about it with us!
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:lovewins:
image: https://www.psxhax.com/attachments/...irmware-rumor-by-cobra-ode-reseller-jpg.2358/

کپی از سایت
Brazilian PS4 Method for 4.50 Firmware Rumor by Cobra ODE Reseller
تیم دانگل کبرا :::: تیم ما از روش "هک برزیلی" دانلود بازی به روی PS4 با سیستم عامل 4.50 را پیدا کرده
Brazilian PS4 Method for 4.50 Firmware Rumor by Cobra ODE Reseller
Since correcting concerns here last month while others go unnoticed, we've included 'Rumor' in this article's title per our updated Site News Posting Guidelines to reflect that this topic should be considered a RUMOR as such.
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:stop:
Now that everyone is clear on that... recently we've heard PS4 4.50 injection rumors reminiscent of those on PS3, so I replied to a few private messages with essentially what you see posted in my reply HERE asking someone who knows more to come forward.
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:notworthyxf2:
Those who've been following the PS4 scene are already familiar with PlayStation 4 GameSharing and the Russian / Egyptian / Xmax Katsu hardware variants of it, but what we found out about today from @Bassabov in the PSXHAX Shoutbox is that official Team Cobra ODE Reseller MagicDevice.ru (see HERE as Cobra's fly-by-night domain is suspended at the time of writing) claims to have revived the Brazilian PS4 GameSharing Method for 4.50 Firmware... that's the current RUMOR anyway!
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:unsurexf2:
Here's what their page states, to quote roughly translated: "PS4: The Brazilian method is the return News - PS4 (10/04/2017 15:45)
Great news! Our team revived the "Brazilian method" of downloading games on the PS4 with the firmware 4.50.
And so, again the Brazilian method works!
1. Fast download of games to your PS4 (from 1 to 3 days)
2. Any firmware, including 4.50
3. Any model PS4 (Fat, Slim, PRO) and any region.
4. Download both to internal and external HDD
5. While ONLINE NO !!! (But we are working on this issue)
6. To download games by our method, the attachment is disassembled!
7. Guarantee from our SC!
A list of games in the PS4 section of our site. We are waiting for orders!"
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:stop: Needless to say, don't pay anyone for harddrives with preloaded PS4 games on them regardless of whether they are rumored to be working on PS4 4.50 Firmware or not... and also don't pay $5,000 (~5 BTC) for the method being used by dark web con-artists and opportunists.
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:slap:
If this RUMOR ends up being legitimate (hopefully Team Cobra ODE screens their business associates to some degree of credibility before including them on their official reseller list
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:cautiousxf2
image: https://www.psxhax.com/styles/default/xenforo/clear.png
:lovewins:
image: https://www.psxhax.com/attachments/...irmware-rumor-by-cobra-ode-reseller-jpg.2358/
کپی از سایت
Brazilian PS4 Method for 4.50 Firmware Rumor by Cobra ODE Reseller
.Nicolas.
کاربر سایت
شایعه:تیم کبرا روش هک برزیلی را دوباره احیا میکند
طبق گفته ی یکی از فروشندگان رسمی تیم کبرا،سازنده شبیه ساز درایو نوری (Cobra Ode) و دانگل Cobra,این تیم روشی را توسعه داده است که به کمک آن میتوان از روش جیلبریک برزیلی دوباره استفاده کرد.
آنها اعلام کرده اند که این روش بر روی آخرین ورژن نیز قابل اجرا است.(آخرین ورژن کنونی 4.50)
همچین اعلام شده،این روش بر روی تمامی مدل ها اعم از PS4 Pro,Slim,Fat قابل استفاده است و بازیها هم بر روی هارد اکسترنال و هم اینترنال قابل دانلود هستند.
طبق خبر منتشر شده،قابلیت آنلاین شدن وجود ندارد اما مشغول کار بر روی استفاده از این قابلیت هستند.
طبق گفته ی یکی از فروشندگان رسمی تیم کبرا،سازنده شبیه ساز درایو نوری (Cobra Ode) و دانگل Cobra,این تیم روشی را توسعه داده است که به کمک آن میتوان از روش جیلبریک برزیلی دوباره استفاده کرد.
آنها اعلام کرده اند که این روش بر روی آخرین ورژن نیز قابل اجرا است.(آخرین ورژن کنونی 4.50)
همچین اعلام شده،این روش بر روی تمامی مدل ها اعم از PS4 Pro,Slim,Fat قابل استفاده است و بازیها هم بر روی هارد اکسترنال و هم اینترنال قابل دانلود هستند.
طبق خبر منتشر شده،قابلیت آنلاین شدن وجود ندارد اما مشغول کار بر روی استفاده از این قابلیت هستند.
کاربرانی که این گفتگو را مشاهده میکنند
مجموع: 1 (اعضا: 0, مهمانها: 1)
به اشتراک گذاری:


