آخرین ویرایش:
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
گزینههای بیشتر
مشارکت کنندگان در این گفتگوTHE BEST BOY
کاربر سایت
آهان ...
پس رعایت قانون کپی رایت و حفظ حقوق ناشر هم شما آزاد کردید واقعا خدا اجرتون بده ممنون خیالم راحت شد.عذاب وجدان داشتم.
دوست عزيز تيتر تاپيك مربوط به خبرهاي هك PS4 هستش.
خواهشا جو تاپيك را به هم نزنيد. هر كي هم آزاده هر بلايي بخواد سر كنسولش بياره و قطعا كسي نميتونه براش تعيين تكليف كنه.
فقط اين كه ما داريم بازي ها را با دو سه برابر قيمت تو ايران ميخريم ربطي به قانون كپي رايت نداره و فقط داريم جيب دلالا را پر پول ميكنيم. بخاطر همين اين كه كپي بازي كني يا با اين قيمتا بازي را بخري هيچ فرقي به حال سازندش نداره. ( تو ايران ) هر موقع قانون كپي رايت تو ايران اومد و از همه مهم تر همه فقط اوج احترام به سازنده را تو خريد بازي اورجينال با چند برابر قيمت نديدن ميشه در موردش بحث كرد.
آخرین ویرایش:
hosseinh
کاربر سایت
دوست عزيز تيتر تاپيك مربوط به خبرهاي هك PS4 هستش.
خواهشا جو تاپيك را به هم نزنيد. هر كي هم آزاده هر بلايي بخواد سر كنسولش بياره و قطعا كسي نميتونه براش تعيين تكليف كنه.
فقط اين كه ما داريم بازي ها را با دو سه برابر قيمت تو ايران ميخريم ربطي به قانون كپي رايت نداره و فقط داريم جيب دلالا را پر پول ميكنيم. بخاطر همين اين كه كپي بازي كني يا با اين قيمتا بازي را بخري هيچ فرقي به حال سازندش نداره. ( تو ايران ) هر موقع قانون كپي رايت تو ايران اومد و از همه مهم تر همه فقط اوج احترام به سازنده را تو خريد بازي اورجينال با چند برابر قيمت نديدن ميشه در موردش بحث كرد.
نظر بنده به ايشان نزديكتر است. آحاد ملت اين را بدانند!
آخرین ویرایش:
PS4 1.76 System Dump on Firmware 1.76 via FTP and File Analysis
سلام
ویتا که یک ماهی میشه هک شده
امروز هم wii هک شد
Wii U Jailbreak Method to Run Game Backups via Modding Tickets
“Brazilian USB Loader”: The hack that sets the Wii U scene on fire again
یدونه ps4 و ایکس وان موندن
انشالله اونم چند روز هک میشه
Today eXtreme posted a PlayStation 4 Model CUH-1116A Firmware 1.760.001 System Dump done via PS4 FTP complete with a File Analysis for developers to examine with the previously released Tools Package.  umpkin:
umpkin:
To quote: PS4 1.76 DUMP
PlayStation 4 - Firmware 1.76 - System Dump - Dumped Filesystem for everyone to look at it or to examine. Should be complete apart from the Sandbox directory. Dumped on FW 1.76 via FTP.
PS4 Model: CUH-1116A
Firmware: 1.760.001
Dumped: 26-04-16
Files: 1.546
Size: 789 MB
To quote from the e✘treme File Analysis page, roughly translated:
System Information (settings / System) -> name / IP address
system_data/settings/system.dat

Profile -> User
user/home/10000000/username.dat

Database -> Home Screen
system_data/priv/mms/app.db

User Application -> Icon
user / appmeta / CUSAXXXXX / icon0.png
System Application -> Icon
system_ex / app / NPXSXXXXX / sce_sys / icon0.png
Trophies -> Number
user / home / user_number / trophy / data / sce_trop / trpsummary.dat
Font
preinst / common / font / DFHEI5-SONY.ttf
Update History
user / appmeta / CUSAXXXXX / change info / changeinfo.xml
Home Menu Sound
preinst / priv / systembgm / bgm_main.at9
Login Sound
preinst / priv / systembgm / bgm_login.at9
Fault History (Settings / Control)
system_data / priv / error / history / 00000001.json

User Authentication
system_data / priv / home / 10000000 / np / auth.dat
EULA (Settings / Control)
update / eula.xml

Below are some related articles for those interested as well:

 umpkin:
umpkin:To quote: PS4 1.76 DUMP
PlayStation 4 - Firmware 1.76 - System Dump - Dumped Filesystem for everyone to look at it or to examine. Should be complete apart from the Sandbox directory. Dumped on FW 1.76 via FTP.
PS4 Model: CUH-1116A
Firmware: 1.760.001
Dumped: 26-04-16
Files: 1.546
Size: 789 MB
To quote from the e✘treme File Analysis page, roughly translated:
System Information (settings / System) -> name / IP address
system_data/settings/system.dat
Profile -> User
user/home/10000000/username.dat
Database -> Home Screen
system_data/priv/mms/app.db
User Application -> Icon
user / appmeta / CUSAXXXXX / icon0.png
System Application -> Icon
system_ex / app / NPXSXXXXX / sce_sys / icon0.png
Trophies -> Number
user / home / user_number / trophy / data / sce_trop / trpsummary.dat
Font
preinst / common / font / DFHEI5-SONY.ttf
Update History
user / appmeta / CUSAXXXXX / change info / changeinfo.xml
Home Menu Sound
preinst / priv / systembgm / bgm_main.at9
Login Sound
preinst / priv / systembgm / bgm_login.at9
Fault History (Settings / Control)
system_data / priv / error / history / 00000001.json
User Authentication
system_data / priv / home / 10000000 / np / auth.dat
EULA (Settings / Control)
update / eula.xml
Below are some related articles for those interested as well:
- PS4 Kernel Exploit Root FS Dump and List of PIDs
- PS4 Filesystem Root Dump, Linux, Fail0verflow & CCC
- Obtaining Your PlayStation 4 SFlash via PS4 Root FTP Server Guide
- PS4 EEPROM Dumper to Dump PlayStation 4 Non-Volatile Storage
- PS4 ShellUI Debug Functions Revealed & Kernel Dumped by OwlBin
- Create PS4 ELFs from PlayStation 4 Process Dumps Guide by Zecoxao
سلام
ویتا که یک ماهی میشه هک شده
امروز هم wii هک شد
Wii U Jailbreak Method to Run Game Backups via Modding Tickets
“Brazilian USB Loader”: The hack that sets the Wii U scene on fire again
یدونه ps4 و ایکس وان موندن
انشالله اونم چند روز هک میشه
Last edited by a moderator:
سلام
دوستان خواهشا در این مورد دیگه بحث نکنید
تاپیک رو قفل میکننا
ممنون
دوستان خواهشا در این مورد دیگه بحث نکنید
تاپیک رو قفل میکننا
ممنون
آخرین ویرایش:
kurosh900
کاربر سایت
Today at the GeekPwn 2016 Carnival in Shanghai Station the Pavilion Safety Research Lab shared a PS4 4.01 Linux installation / Ksploit demonstration exploit video via Chinese site Changting Technology Security Lab! 
In the video they navigate their PS4 Web browser to 长亭安全研究实验室-破解最新PS4 which currently just shows their video instead of their 'Sony PlayStation4 Jailbreak' so hopefully more details on this PS4 jailbreak method will follow soon!
Check it out below with some related Tweets from Joonie86, who also notes they played Mario using an NES emulator as follows
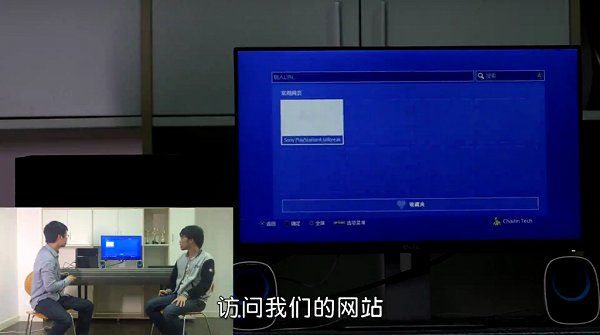
یه گروه چینی تونسته که تو فریمور 4.0.1 لینوکس رو نصب کنه و از طریق شبیه ساز کنسول nes بازی ماریو رو اجرا کنه.
اینجور که مشخصه سحر نزدیک است!
In the video they navigate their PS4 Web browser to 长亭安全研究实验室-破解最新PS4 which currently just shows their video instead of their 'Sony PlayStation4 Jailbreak' so hopefully more details on this PS4 jailbreak method will follow soon!

Check it out below with some related Tweets from Joonie86, who also notes they played Mario using an NES emulator as follows
یه گروه چینی تونسته که تو فریمور 4.0.1 لینوکس رو نصب کنه و از طریق شبیه ساز کنسول nes بازی ماریو رو اجرا کنه.
اینجور که مشخصه سحر نزدیک است!
نخیر دوستمون درست میگه قانون کپی رایت میگه که شما دستگاهی که خریدید میتونید هک یا هر کاره دیگه ای بکنید فقط حق اینو ندارید که این هک رو انتشار بدیدآهان ...
پس رعایت قانون کپی رایت و حفظ حقوق ناشر هم شما آزاد کردید واقعا خدا اجرتون بده ممنون خیالم راحت شد.عذاب وجدان داشتم.
Behnams923
کاربر سایت
More Details surface on the PS4 4.01 Jailbreak, potentially enough for a public release “soon”
The PS4 scene has been doing a bit of detective work to understand the exploits behind the 4.01 Jailbreak that was demonstrated yesterday in Shanghai. After the hackers of Taichin Tech announced they would disclose the exploits to Sony, people were able to find data about the exploit on the FreeBSD mailing list and bug tracker.
Of course, not everyone can do much with this information, but in theory the details of how the bug was fixed should be enough information for people with the right set of skills to cause a kernel panic on the PS4. How that is later used to gain control of the PS4 will be let as an exercise to the people who know what they’re doing. Oh, and naturally, you’d also need a user entry point, some sort of Webkit exploit or something, in order to be able to execute the code in the first place.
The Kernel exploit itself apparently relies on a CVE (CVE-2016-1885) that was revealed back in April. It seems that this was not properly patched and this is one of the flaws the security researchers at Taichin Tech used to gain access to the PS4 system.
The argument validation in r296956 was not enough to close all possible overflows in sysarch(2)
Modified:
stable/9/sys/amd64/amd64/sys_machdep.c
Directory Properties:
stable/9/ (props changed)
stable/9/sys/ (props changed)
Modified: stable/9/sys/amd64/amd64/sys_machdep.c
==============================================================================
--- stable/9/sys/amd64/amd64/sys_machdep.c Tue Oct 25 17:16:08 2016
(r307940)
+++ stable/9/sys/amd64/amd64/sys_machdep.c Tue Oct 25 17:16:58 2016
(r307941)
@@ -612,6 +612,8 @@ amd64_set_ldt(td, uap, descs)
largest_ld = uap->start + uap->num;
if (largest_ld > max_ldt_segment)
largest_ld = max_ldt_segment;
+ if (largest_ld < uap->start)
+ return (EINVAL);
i = largest_ld - uap->start;
mtx_lock(&dt_lock);
bzero(&((struct user_segment_descriptor *)(pldt->ldt_base))
@@ -624,7 +626,8 @@ amd64_set_ldt(td, uap, descs)
/* verify range of descriptors to modify */
largest_ld = uap->start + uap->num;
if (uap->start >= max_ldt_segment ||
- largest_ld > max_ldt_segment)
+ largest_ld > max_ldt_segment ||
+ largest_ld < uap->start)
return (EINVAL);
}
There are lots of “ifs” here, but with the kernel exploit pretty much in the open, it sounds like a public release is now in the realm of the possible, assuming the right people decide to work on a release.

Relevant links:
Source: via psxhax, thanks to everyone who pointed me to the article.
Share
0
2
The PS4 scene has been doing a bit of detective work to understand the exploits behind the 4.01 Jailbreak that was demonstrated yesterday in Shanghai. After the hackers of Taichin Tech announced they would disclose the exploits to Sony, people were able to find data about the exploit on the FreeBSD mailing list and bug tracker.
Of course, not everyone can do much with this information, but in theory the details of how the bug was fixed should be enough information for people with the right set of skills to cause a kernel panic on the PS4. How that is later used to gain control of the PS4 will be let as an exercise to the people who know what they’re doing. Oh, and naturally, you’d also need a user entry point, some sort of Webkit exploit or something, in order to be able to execute the code in the first place.
The Kernel exploit itself apparently relies on a CVE (CVE-2016-1885) that was revealed back in April. It seems that this was not properly patched and this is one of the flaws the security researchers at Taichin Tech used to gain access to the PS4 system.
The argument validation in r296956 was not enough to close all possible overflows in sysarch(2)
Modified:
stable/9/sys/amd64/amd64/sys_machdep.c
Directory Properties:
stable/9/ (props changed)
stable/9/sys/ (props changed)
Modified: stable/9/sys/amd64/amd64/sys_machdep.c
==============================================================================
--- stable/9/sys/amd64/amd64/sys_machdep.c Tue Oct 25 17:16:08 2016
(r307940)
+++ stable/9/sys/amd64/amd64/sys_machdep.c Tue Oct 25 17:16:58 2016
(r307941)
@@ -612,6 +612,8 @@ amd64_set_ldt(td, uap, descs)
largest_ld = uap->start + uap->num;
if (largest_ld > max_ldt_segment)
largest_ld = max_ldt_segment;
+ if (largest_ld < uap->start)
+ return (EINVAL);
i = largest_ld - uap->start;
mtx_lock(&dt_lock);
bzero(&((struct user_segment_descriptor *)(pldt->ldt_base))
@@ -624,7 +626,8 @@ amd64_set_ldt(td, uap, descs)
/* verify range of descriptors to modify */
largest_ld = uap->start + uap->num;
if (uap->start >= max_ldt_segment ||
- largest_ld > max_ldt_segment)
+ largest_ld > max_ldt_segment ||
+ largest_ld < uap->start)
return (EINVAL);
}
There are lots of “ifs” here, but with the kernel exploit pretty much in the open, it sounds like a public release is now in the realm of the possible, assuming the right people decide to work on a release.

Relevant links:
- FreeBSD Security Advisory
- CVE-2016-1885
- Bug fix with details on what was broken
Source: via psxhax, thanks to everyone who pointed me to the article.
Share
0
2
Kun Yang of Chaitin Tech on PS4 4.01 Jailbreak, OFW 4.05 Untested
Yesterday we saw their Full Demo Video, and today Kun Yang of the Chinese PS4 4.01 Jailbreakers Chaitin Tech responded via e-mail to @mcmrc1 who reached out to them with some questions about their recent PlayStation 4 exploit. :hushedface:
Check out the e-mail response image and related Tweets from mcmrc1 below, and in summary they invite all PlayStation 4 fans to follow their Chaitin Tech Twitter for updates on their PS4 Jailbreak, they are still awaiting word back from Sony on their bug submission and have not yet tested their exploit on PS4 Firmware 4.05 to see if it's been patched yet.

Thanks to @B7U3 C50SS for the tipoff in the PSXHAX Shoutbox (and PM), and a VERY SPECIAL THANKS to @mcmrc1 for reaching out to the Chaitin Team and keeping us all in the loop here! [img src="https://www.psxhax.com/styles/default/xenforo/clear.png" class="mceSmilieSprite mceSmilie164" alt="<3>

Yesterday we saw their Full Demo Video, and today Kun Yang of the Chinese PS4 4.01 Jailbreakers Chaitin Tech responded via e-mail to @mcmrc1 who reached out to them with some questions about their recent PlayStation 4 exploit. :hushedface:
Check out the e-mail response image and related Tweets from mcmrc1 below, and in summary they invite all PlayStation 4 fans to follow their Chaitin Tech Twitter for updates on their PS4 Jailbreak, they are still awaiting word back from Sony on their bug submission and have not yet tested their exploit on PS4 Firmware 4.05 to see if it's been patched yet.
Thanks to @B7U3 C50SS for the tipoff in the PSXHAX Shoutbox (and PM), and a VERY SPECIAL THANKS to @mcmrc1 for reaching out to the Chaitin Team and keeping us all in the loop here! [img src="https://www.psxhax.com/styles/default/xenforo/clear.png" class="mceSmilieSprite mceSmilie164" alt="<3>
PlayStation 4 DevKit / TestKit PS4UPDATE PUP Archive by MrNiato
After his PS4 TestKit DEX Console Manager demo video and PS4UPDATE-TestKit-GEN3-3_508_041.PUP for PlayStation 4 developers, @MrNiato has since started MrNiato's Blog and shared some PS3 DECH (DEX) and DECR (Reference Tool) PUP's alongside PlayStation 4 DevKit / TestKit PS4UPDATE PUP's for those seeking them! :veryhappy:
You can check out all the PS3 and PS4 developer PUP file downloads on MrNiato's Blog HERE along with installation tutorials for PlayStation 3 and PlayStation 4 development console owners.
Below are the PS4 DevKit / TestKit updates he's added thus far:
Download (PS4 TestKit Update):

After his PS4 TestKit DEX Console Manager demo video and PS4UPDATE-TestKit-GEN3-3_508_041.PUP for PlayStation 4 developers, @MrNiato has since started MrNiato's Blog and shared some PS3 DECH (DEX) and DECR (Reference Tool) PUP's alongside PlayStation 4 DevKit / TestKit PS4UPDATE PUP's for those seeking them! :veryhappy:
You can check out all the PS3 and PS4 developer PUP file downloads on MrNiato's Blog HERE along with installation tutorials for PlayStation 3 and PlayStation 4 development console owners.
Below are the PS4 DevKit / TestKit updates he's added thus far:
Download (PS4 TestKit Update):
- 3.508.041: PS4UPDATE-testkit-GEN3-3_508_041.PUP
- 3.150.001: PS4UPDATE-testkit-GEN3-3_150_001.PUP
- 2.000.071: PS4UPDATE-testkit-GEN3-2_000_071.PUP
- 1.760.001: PS4UPDATE-testkit-GEN3-1_760_001.PUP
- 1.501.041: PS4UPDATE-testkit-GEN2-1_501_041.PUP
- 1.500.101: PS4UPDATE-testkit-GEN3-1_500_101.PUP
- 1.750.061: PS4UPDATE-devkit-GEN3-1_750_061.PUP
گفتن به زودی فریمور 4.01 رو میدن بیرون
یعنی ممکنه
یعنی ممکنه
PlayStation 4 DevKit / TestKit PS4UPDATE PUP Archive by MrNiato
After his PS4 TestKit DEX Console Manager demo video and PS4UPDATE-TestKit-GEN3-3_508_041.PUP for PlayStation 4 developers, @MrNiato has since started MrNiato's Blog and shared some PS3 DECH (DEX) and DECR (Reference Tool) PUP's alongside PlayStation 4 DevKit / TestKit PS4UPDATE PUP's for those seeking them! :veryhappy:
You can check out all the PS3 and PS4 developer PUP file downloads on MrNiato's Blog HERE along with installation tutorials for PlayStation 3 and PlayStation 4 development console owners.
Below are the PS4 DevKit / TestKit updates he's added thus far:
Download (PS4 TestKit Update):
Download (PS4 DevKit Update):
- 3.508.041: PS4UPDATE-testkit-GEN3-3_508_041.PUP
- 3.150.001: PS4UPDATE-testkit-GEN3-3_150_001.PUP
- 2.000.071: PS4UPDATE-testkit-GEN3-2_000_071.PUP
- 1.760.001: PS4UPDATE-testkit-GEN3-1_760_001.PUP
- 1.501.041: PS4UPDATE-testkit-GEN2-1_501_041.PUP
- 1.500.101: PS4UPDATE-testkit-GEN3-1_500_101.PUP
Thanks to @REBUG25 for the tip in the Shoutbox and once again to @MrNiato for breathing some life into the PS4 development console scene! :music:
- 1.750.061: PS4UPDATE-devkit-GEN3-1_750_061.PUP

کسی بخواد خبر انگلیسی بخونه میاد اینجا به نظرت؟؟؟؟؟؟؟؟؟؟؟؟؟؟؟؟؟
اینارو ترجمه کن!!!!! خیلی خوبه اینا رو بفهمیم
hamedm1
کاربر سایت
من که ps4 برای امتحان کردن ندارم طبق خبر ها یسری هکر های چینی مثل اینکه تونستن 4.01 و هک کنن البته سونی برای مقابله برای این هک سریع اپدیت بعدیو بیرون داد این هکیم اومده فلن اول کاره و مثل ps vita فلن یسری emulator و اجرا می کنه
Sony+
کاربر سایت
به نظر من هم لطفا خبرها رو فارسی بذارید و خلاصه فارسیش کنید.
من که ps4 برای امتحان کردن ندارم طبق خبر ها یسری هکر های چینی مثل اینکه تونستن 4.01 و هک کنن البته سونی برای مقابله برای این هک سریع اپدیت بعدیو بیرون داد این هکیم اومده فلن اول کاره و مثل ps vita فلن یسری emulator و اجرا می کنه
 من احتمال دادم سرکاریه ولی مثل این که واقعا هک شده !
من احتمال دادم سرکاریه ولی مثل این که واقعا هک شده !امیدوارم یه راه دانگرید هم از 4.05 پیدا کنن برای این فریمور ...
کاربرانی که این گفتگو را مشاهده میکنند
مجموع: 2 (اعضا: 0, مهمانها: 2)
به اشتراک گذاری:


